
My January Challenge
It is January 2024. This month, I have a challenge of Blogging. It is to publish one post per day. It’s very hard for me. I have never tried it before. I will focus on blogging only. I will not...
Tech geek. Life geek.

It is January 2024. This month, I have a challenge of Blogging. It is to publish one post per day. It’s very hard for me. I have never tried it before. I will focus on blogging only. I will not...
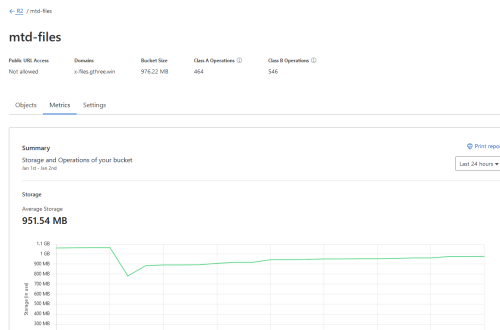
I have been using Cloudflare R2 for Mastodon media storage for almost a week. Let me see what the status of this bucket is and how much storage it takes. The Cloudflare R2 Bucket information See, the Bucket size is...
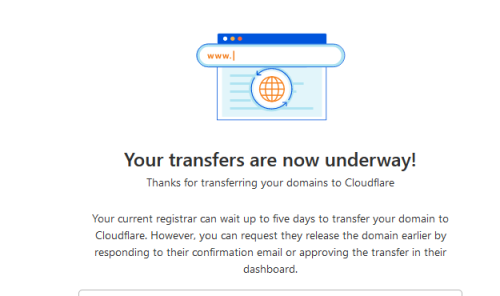
This week, I am doing domain names winter clean. I have a lot of domain names that need to be maintained. How many domain registrars do I use? About twenty years ago, I registered my first Domain name at 1and1....
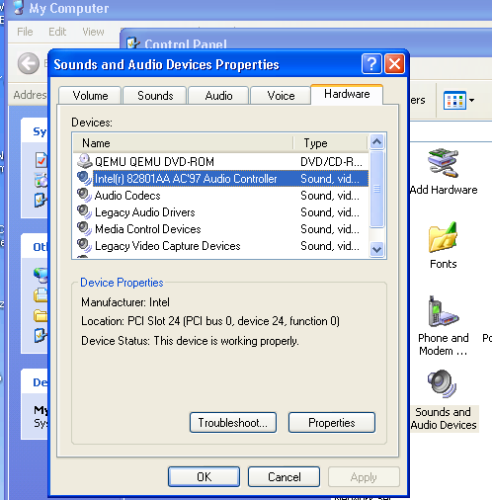
Here is the situation. The host is the Proxmox VE system. The guest system is Windows XP SP3. The problem is I can play sound in this Windows XP. I know the noVNC has no sound. How to enable audio?...

It is already 2024. I would like to look back and see what I did in the past year. How many posts have I published in 2023? Yinfor.com 80 blog posts journal.yinfor.com 11 blog posts seo.g2soft.net 21 blog posts So,...
Yes, a few days ago, I started to use Cloudflare R2 for my Mastodon media storage. There are three steps. 1) Download all the media files from Backblaze B2 2) Upload the files of step 1 to Cloudflare R2 3)...

Today, when I checked the old emails of my second Gmail account, I saw an email with an update notice. I started to use Matomo on this blog in May 2023. Matomo Analytics 5.0 is here What’s new? * Strengthened...

It is almost 2024. We have the Jiaozi (Dumplin) for dinner. Everyone in my family does it together. I prepared the stuffing. Mainly are ground pork 500g, Napa cabbage 1500g. Chopped napa, and pressed them to get off the water....

I have been using Backblaze B2 Storage for fifteen days. In the beginning, the data was not stable. I changed the settings multiple times. The Backblaze backend reporting is kind of delayed or 48 hours round. Today, I will recheck...
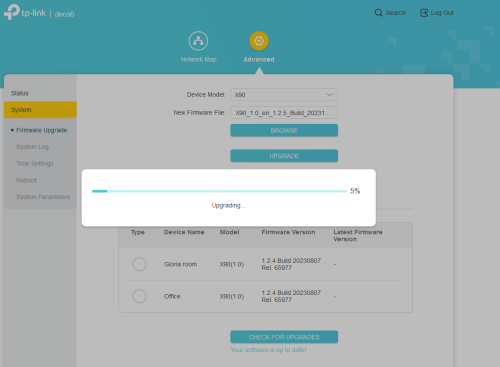
Almost every three months, I will try to upgrade the device firmware. Here are the simple records for today’s updates. Upgrade the TP-Link Switch. The latest one is v1.0.13. After the upgrade, it will reboot automatically. It is a...

I received an email from ICBC. It is a great reminder for the drivers in BC. It also provides some important facts here. 32% of crashes happend in parking lots. Holiday shopping season is here! While it’s always important to...
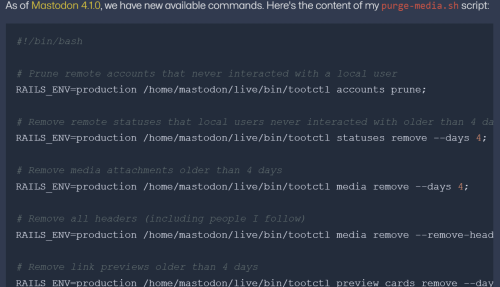
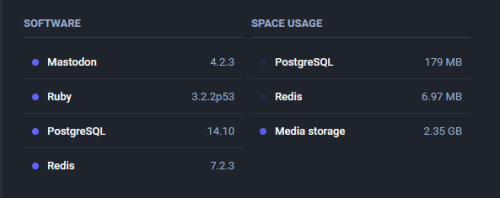
When I post the Mastodon Self-hosting – Clean Media Storage with tootctl command, I forget to record how I prepare the environment. Before I run the tootctl command, I did the following. I checked the version of tootctl.

In the last post, I mentioned that my Gitlab CE space was used very fast. In 4 months, I have to expand the disk space again. The folder /var/opt/gitlab/prometheus/data/wal is more than 85GB. There are so many files in the...
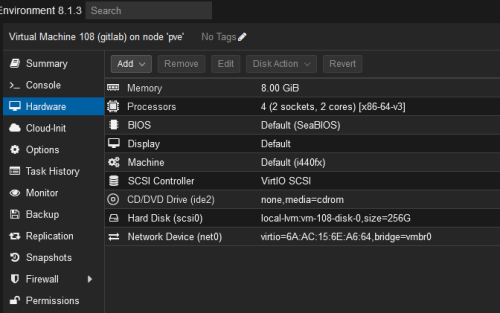
It is the second time I have expanded the disk on Proxmox VE. I have a post about how to expand the VM disk in Proxmox VE. The host is Proxmox VE v8.1.3. The guest is a Gitlab on Ubuntu...
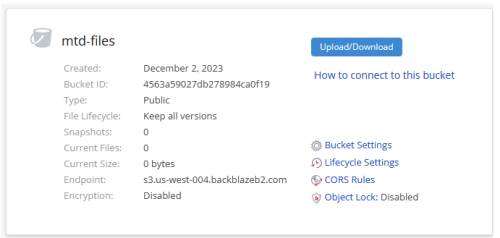
Set up Backblaze B2 storage with existing Mastodon. Here is for my record, not as a guide or reference. If you follow it on your Mastodon instance, take a risk. I use the Backblaze B2 storage after a few days...