
Canon imageCLASS MF284dw
My old Canon imageClass MF4450 is about 14 years old. The tonner was changed many times. The printer hinges were replaced as well. Recently, I found the image or text printed on the paper had faded quickly. Asked the AI,...
Tech geek. Life geek.

My old Canon imageClass MF4450 is about 14 years old. The tonner was changed many times. The printer hinges were replaced as well. Recently, I found the image or text printed on the paper had faded quickly. Asked the AI,...
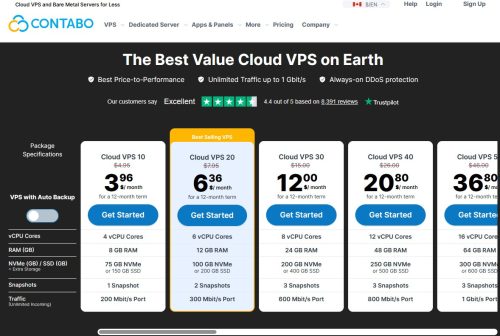
Now, after two years, I try to use Contabo VPS again. Today, I ordered a new Contabo VPS 20. The best-selling VPS of Contabo. Annual payment is $76.32 for 12 months, which is about $6.36/month. When I SSH to the...
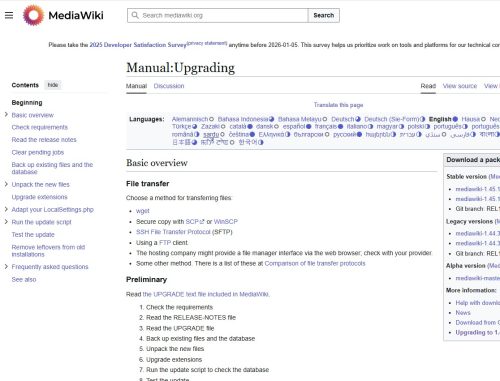
I am upgrading the Mediawiki installation from 1.44.2 to 1.45.1. Everything is OK. Until I try the update script. I forgot to record the error. So I found one on the Web. As below 15:47:42 [250e8a55b4df40e8c3d5f0dd] [no req] Error: Class...
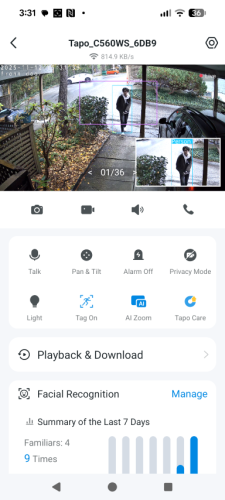
I have been using the Tapo C560WS security camera for a week. As I mentioned in my last post, the camera is installed at the front door of my house. I use it to record events, including people coming in...

Recently, I received a new outdoor security camera from the TP-Link system, Tapo C560WS. It was announced on June 24, 2025. It is quite a bit heavy. I can feel it is a good quality. Here is the list of...

I have two TP-Link security cameras that I purchased in July 2025. I bought the first one at Amazon.ca. TP-Link Tapo 2K 4MP QHD Security Camera Outdoor Wired, built-in Siren w/Startlight Sensor, IP66 Weatherproof, Motion/Person Detection, Works with Alexa &...

Wow, TP-Link just dropped a press announcement about the WiFi 8 era. I can’t believe it’s already here! TP-Link, a leading global provider of consumer and business networking products, announced it has successfully demonstrated Wi-Fi 8 connectivity, transmitting data with...
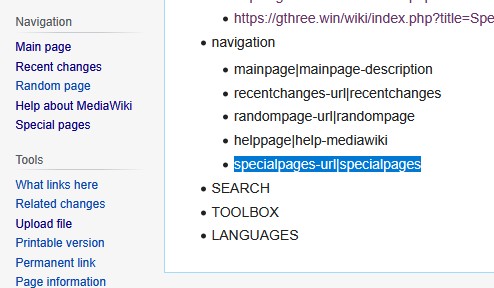
I have a Wiki site installation at my Homelab server. I tried to keep it updated every time MediaWiki has a new release. Last week, I upgraded my Wiki from 1.43.1 to 1.44.0. Look at it. There is a Deprecation...
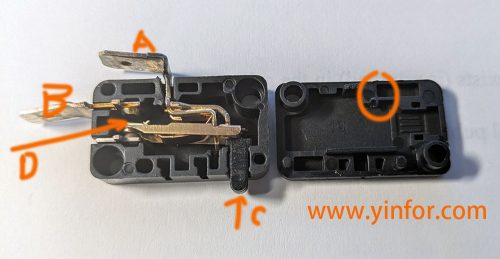
I have a Kalorik Air Fryer, which I bought at Costco four years ago. Last week, during the process of air frying the fish sticks, it stopped working suddenly. No lights on. I thought it might be that the power...
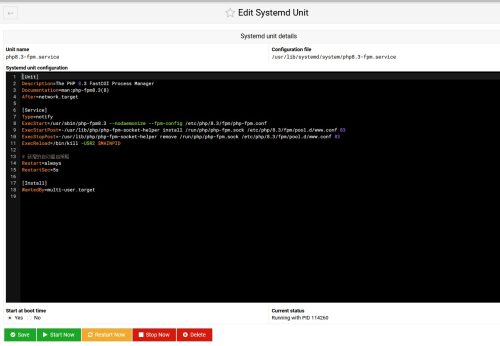
There is an incident on one of my websites this morning. It returns a 502 Bad Gateway error when I try to reach the website. I did a little bit of research on the Internet. I found it is because...
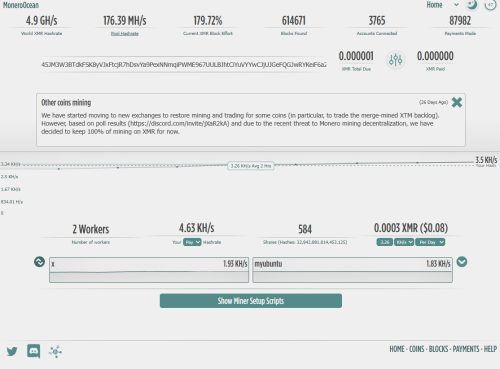
Today, I tried running the Crypto Mining on my two PCs. The results are fun. I asked everything on the Microsoft Copilot desktop App. It explained which crypto is good for CPU mining, how to get the software, how to...
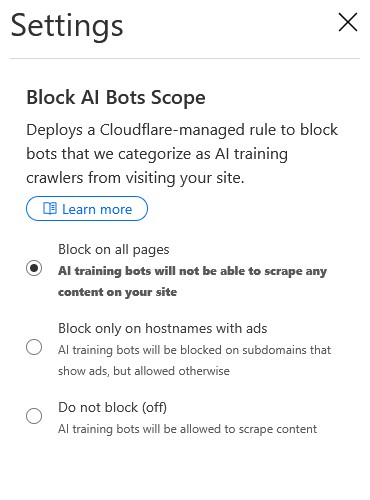
I think it is best to block AI bots. I use Cloudflare as the CDN for the whole website. It is quite easy to make it happen. Cloudflare AI Bots setting You can choose to block AI bots by activating...
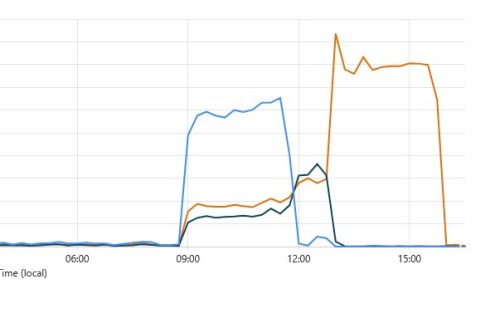
Here we go. I found the websites are not available at noon. I checked the server status. All good. But the websites return a 404 error. OK, I just restarted the PHP-FPM service. Because the static page is OK. So...
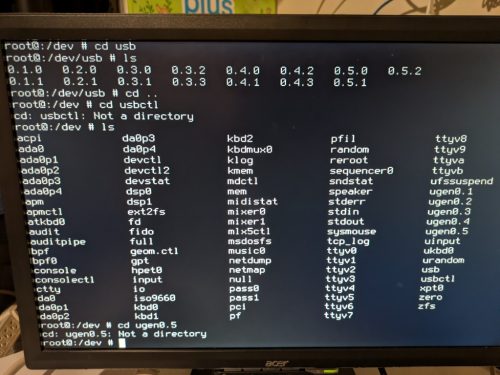
One night, the router is stopping working. It is powered by OPNsense. So, how can I do? First, boot it to single-user mode. Reboot, of course, the device is rebooting repeatedly. Enter boot Menu, select the second option. Access shell....
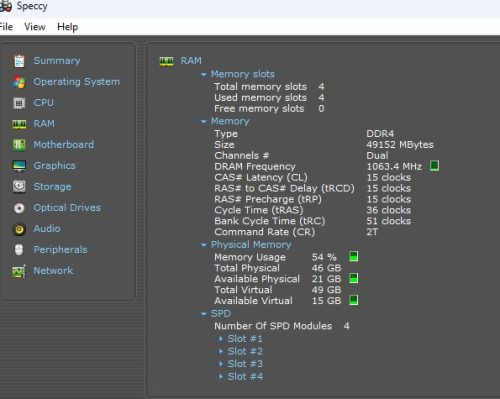
It is a small update. My wife’s old desktop was retired. It has two RAM stickers, 2X8GB. My PC has 2X16GB + 8GB + 4GB. It is kind of unbalanced. Now I have the chance to make it right. These...