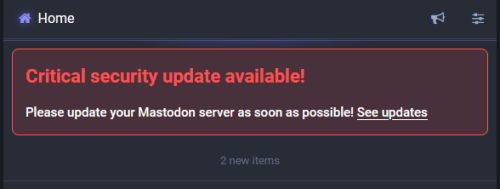
Upgrade Mastodon from 4.2.5 to 4.2.6 to 4.2.7
I just finished the upgrades of my Mastodon instance. I saw this notice a few days ago. I just have no time to do it. I flew to San Francisco last week. To look after my father-in-law. He received surgery...