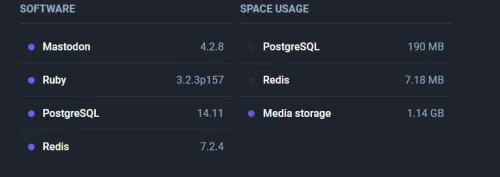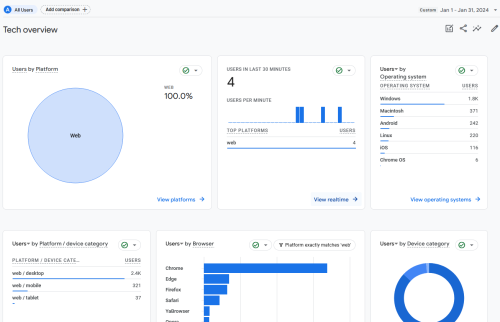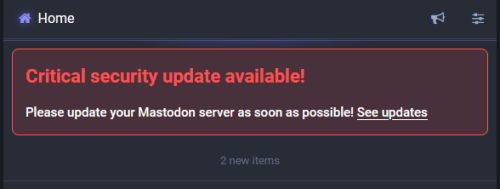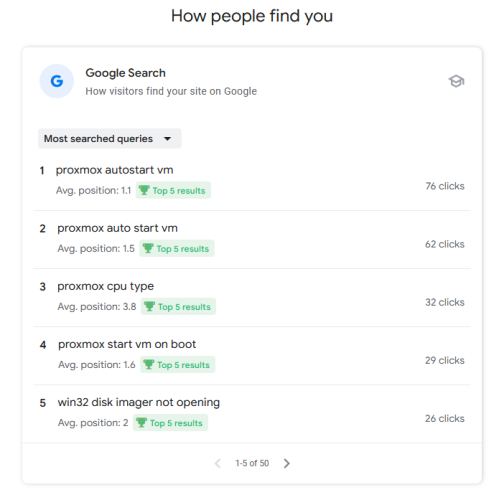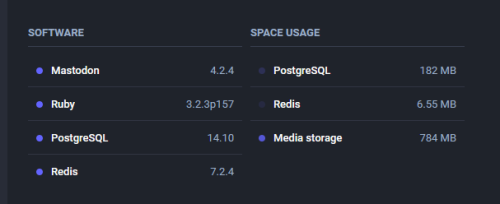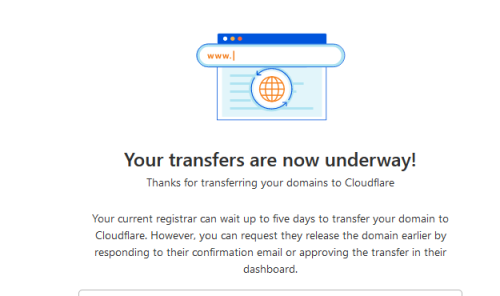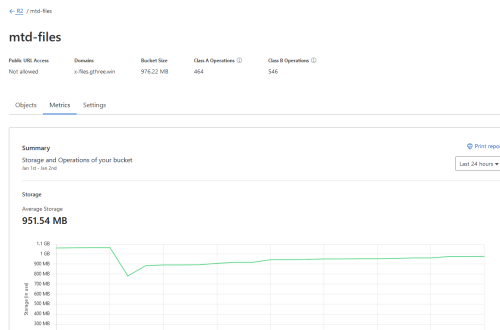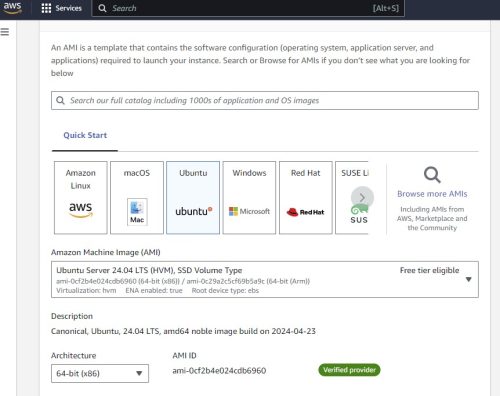
Ubuntu 24.04lts can be deployed on the most VPS provider
Hey, when I say you can deploy Ubuntu 24.04lts on the most mainstream VPS providers, it means someone like DigitalOcean, Linode, AWS, etc. Ubuntu 24.04 Lts is just released in five days. Let’s sign in to my accounts and have...