It is time to block AI bots
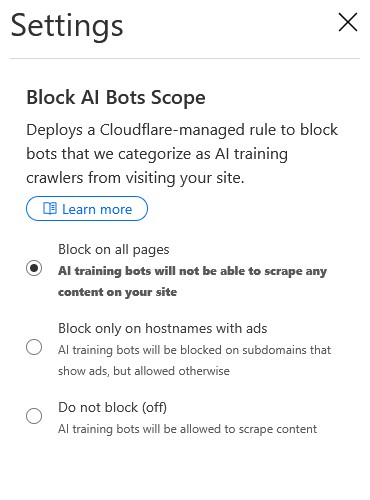
I think it is best to block AI bots. I use Cloudflare as the CDN for the whole website. It is quite easy to make it happen. Cloudflare AI Bots setting You can choose to block AI bots by activating...
Tech geek. Life geek.

I think it is best to block AI bots. I use Cloudflare as the CDN for the whole website. It is quite easy to make it happen. Cloudflare AI Bots setting You can choose to block AI bots by activating...
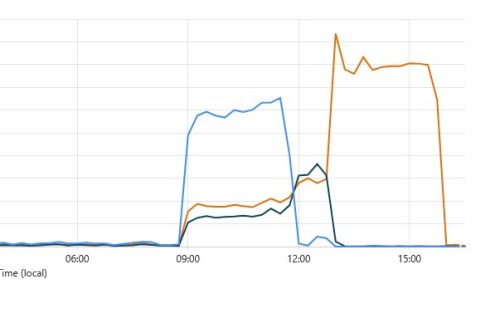
Here we go. I found the websites are not available at noon. I checked the server status. All good. But the websites return a 404 error. OK, I just restarted the PHP-FPM service. Because the static page is OK. So...

Today, I received an email from a website monitoring service. It said my site was down. 1) The very first step is to try the website. The browser can not open it. 2) I sign in to the PVE, and...
I used Sogou Pinyin IME for many years. It is easy to use. Save your time, the conclusion is: Do not use Sogou Pinyin IME. https://shurufa.sogou.com/ Here is the problem I found last month. The blue circle with the mouse...

I just finished the upgrades of my Mastodon instance. I saw this notice a few days ago. I just have no time to do it. I flew to San Francisco last week. To look after my father-in-law. He received surgery...
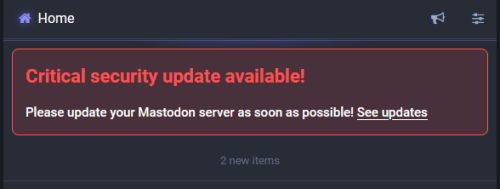
It is just a week since I upgraded my Mastodon from 4.2.3 to v4.2.4. Today, I saw this critical update notice when I checked the Maston instance this morning. So, I went to the official release v4.2.5 notes to see...
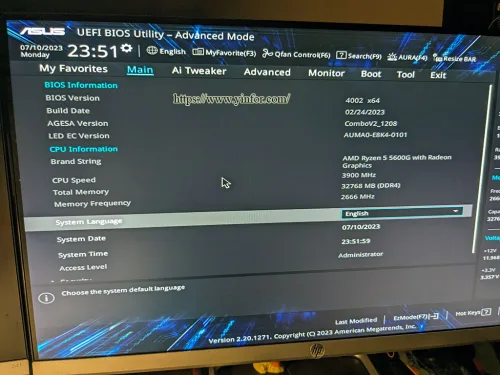
It is time to check the BIOS version of my PC. I do regular maintenance for a few months. The upgrade procedure is the same as before. The motherboard is Asus PRIME B450M-A II. The version of BIOS on the...

Cyberattacks are, in some ways, an invisible and unpredictable threat, but they can have awful consequences for businesses of all sizes. Around a quarter of businesses will fall victim to a cyberattack, so it is important to prepare for the...

Every day, hundreds of people have their smartphone hacked, exposing important data like contacts and even credit card details to criminals that prey upon poorly protected phones. Whenever your phone connects to the internet, it is at risk from hacking...
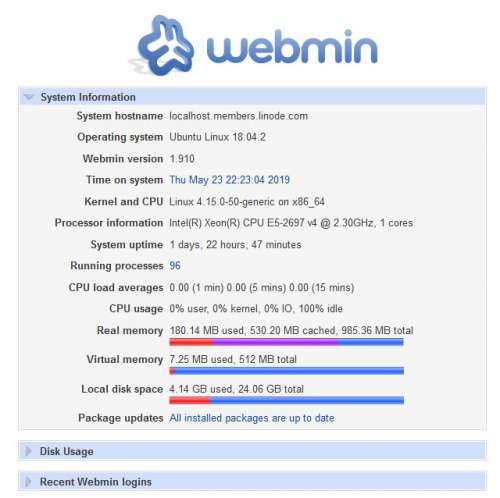
It is a record of how I build an Nginx with Brotli compression and TLS 1.3 support. I use it on my Linode VPS. It is a Nanon type of VPS at Fremont, CA, USA. 1GB RAM, 25GB storage,...
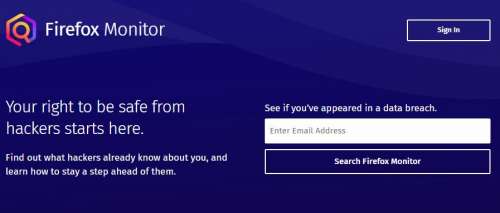
Firefox provides a new service, Firefox Monitor. You can check how much your personal data breach on the Internet. Just enter the email address which you used on the Internet. Click search Firefox Monitor. For example, I entered an email...

540 million data records of Facebook users were compromised after third-party apps and sites stored the data on unsecured servers. The leaked information included comments, likes, reactions, account names, and FB IDs, and some email addresses. The app called At...

Some time ago, on October 8, 2018, Google came out and admitted to a data breach in its Google+ social network, because of a software bug. This bug resulted in close to 500,000 user accounts getting compromised. There is...
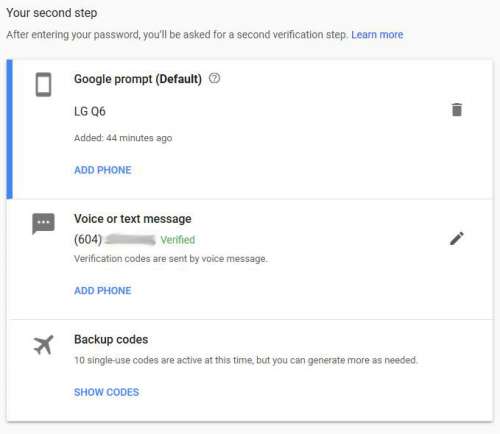
After I change my old smartphone to LG Q6, I would like to transfer all apps to it. I used Google Authenticator for a bunch of websites as the Two-factor Authentication. I just found Google Authenticator cannot move all these...

Visitor Access Management is a tricky subject for security experts. This is especially true for secure locations such as hospitals, schools, and office buildings. Visitor management has two sides to it – location security and visitor hospitality. Neither do you...