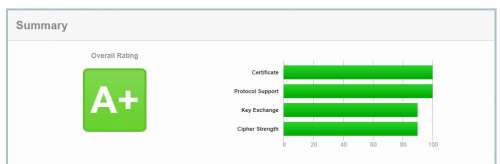
It is easy to get an A+ on your website. But it is a little bit hard to make a 4 parts, Certificate, Protocol Support, Key Exchange, and Cipher Strength, to be 100%.
Most of time, I got A+ rating of my site. For individual scores, the last two are 90%.
Let me break down.
Certificate
It is preaty easy to get 100% here.
- Make sure your certificate and intermediate certificate and CA are in the correct order.
- Don’t use SHA1 for the signature algorithm. Use SHA256 instead. Actually all main CA are using SHA256 now.
- Use a trusted CA. Do not use WoSign, StartCom.
Protocol Support
- SSL 2.0 0%
- SSL 3.0 80%
- TLS 1.0 90%
- TLS 1.1 95%
- TLS 1.2 100%
So it is best to just use TLS 1.2.
Key Exchange
Make a strong DHE (Ephemeral Diffie-Hellman) paramaaters.
openssldhparam -out /etc/nginx/ssl/dhparam.pem 4096
It is not enough. Add following into Nginx settings.
ssl_ecdh_curve secp384r1;
Cipher Strength
- 0 bits (no encryption) 0%
- < 128 bits (e.g., 40, 56) 20%
- < 256 bits (e.g., 128, 168) 80%
- >= 256 bits (e.g., 256) 100%
So I just use 256 bit cipher suites.
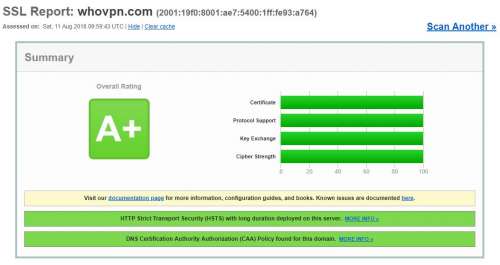
Here is a test site, I tried it today, 2018-08-11. It is A+ with four 100% scores.
Here is the most important part of Nginx config file. I put them all together.
ssl_certificate /etc/nginx/ssl/whovpn.com/fullchain; ssl_certificate_key /etc/nginx/ssl/whovpn.com/key; ssl_session_timeout 10m; ssl_session_cache shared:SSL:10m; ssl_session_tickets off; ssl_dhparam /etc/nginx/ssl/dhparam.pem; # modern configuration. tweak to your needs. ssl_protocols TLSv1.2; ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES256-SHA384'; ssl_prefer_server_ciphers on; ssl_ecdh_curve secp384r1; # HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months) add_header Strict-Transport-Security max-age=15768000; # OCSP Stapling --- # fetch OCSP records from URL in ssl_certificate and cache them ssl_stapling on; ssl_stapling_verify on; ## verify chain of trust of OCSP response using Root CA and Intermediate certs ssl_trusted_certificate /etc/nginx/ssl/whovpn.com/fullchain; resolver 8.8.8.8;