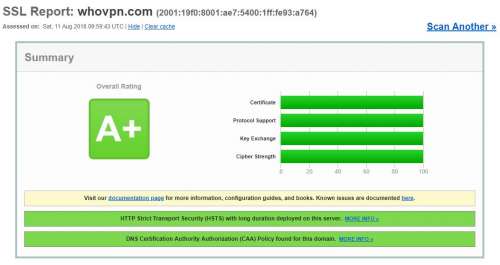
How to get a perfect SSL Labs score
It is easy to get an A+ on your website. But it is a little bit hard to make a 4 parts, Certificate, Protocol Support, Key Exchange, and Cipher Strength, to be 100%. Most of time, I got A+ rating...
Tech geek. Life geek.

It is easy to get an A+ on your website. But it is a little bit hard to make a 4 parts, Certificate, Protocol Support, Key Exchange, and Cipher Strength, to be 100%. Most of time, I got A+ rating...
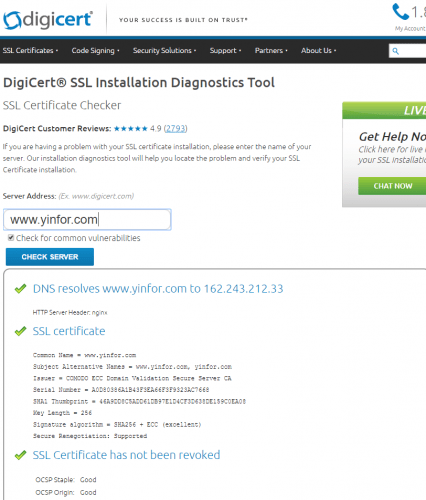
It is 2016, your website must be SSL encrypted. Now, you have questions, how about my server and how about my SSL installation? This is the answer to this question. You must try these five free tools to test, check,...
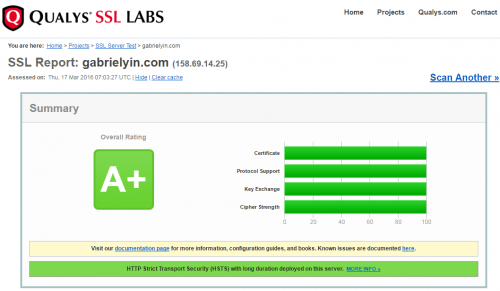
Now, a lot of web site are going to add SSL for security purpose. Just like my site here, the SSL Report is as below. It is A+. The score is great. When I look at it close. There are...