
Firefox always show Performing TLS Handshake
During last two weeks, my firefox getting slower and slower. It is Windows 10, with Firefox 67 or early version. When I enter an HTTPS web site URL into the address bar, it took a lot of time to load...
Tech geek. Life geek.

During last two weeks, my firefox getting slower and slower. It is Windows 10, with Firefox 67 or early version. When I enter an HTTPS web site URL into the address bar, it took a lot of time to load...
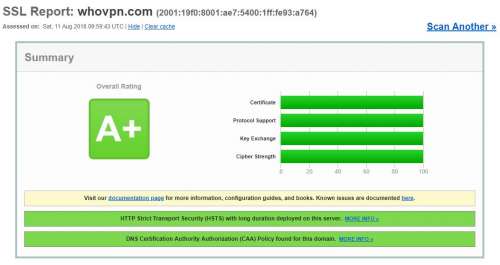
It is easy to get an A+ on your website. But it is a little bit hard to make a 4 parts, Certificate, Protocol Support, Key Exchange, and Cipher Strength, to be 100%. Most of time, I got A+ rating...
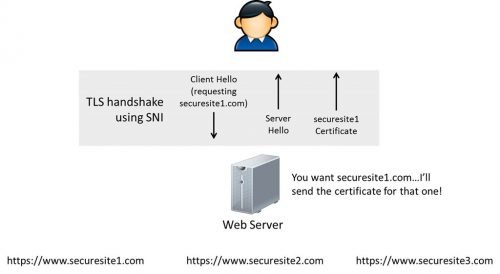
Server Name Indication is an extension to the TLS computer networking protocol by which a client indicates which hostname it is attempting to connect to at the start of the handshaking process. The most import reason to have this extension...
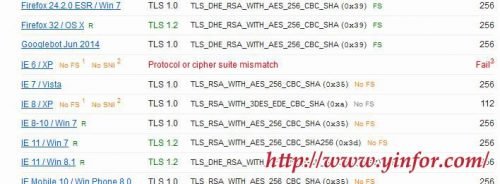
As we always disable SSLv2 in Apache. Now it is SSLv3 turn. The recent news about the SSL 3 vulnerability is so important that I have to disable it as well. So just modify the ssl.conf of Apache [ssh]SSLProtocol All...