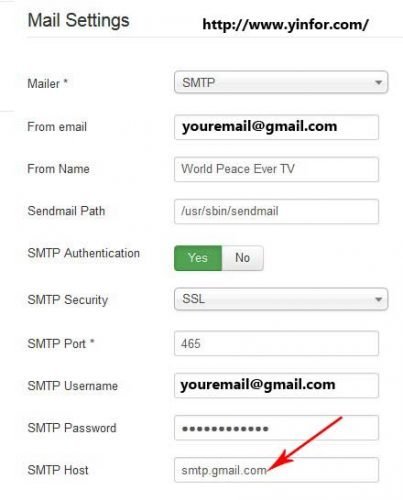
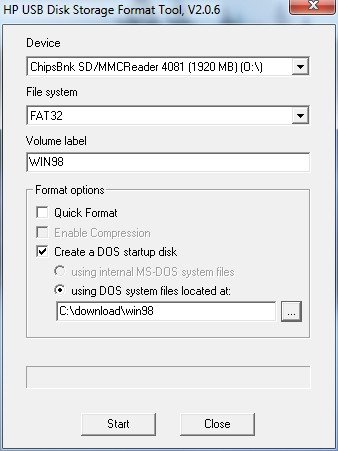
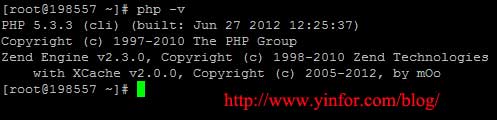
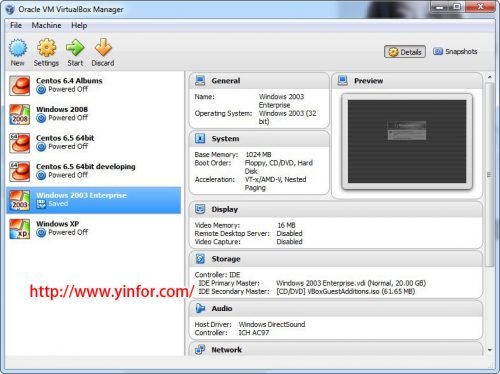
How to config PHP to secure Web Server
There are certain PHP configuration tat affect security features. The following recommended security configuration options is for production servers. register_globals set to off safe_mode set to off error_reporting set to off disable these functions: system(), exec(), passthru(), shell_exec(), proc_open(), and...