SSL Certificate Checker
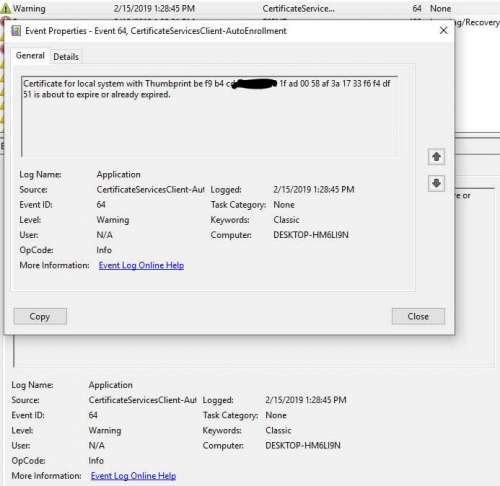
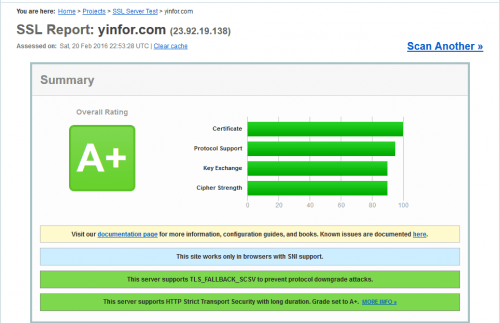
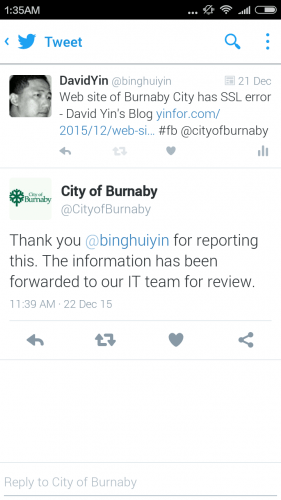
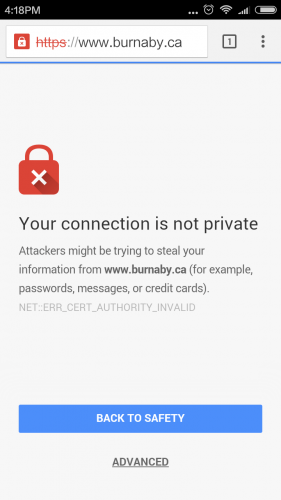
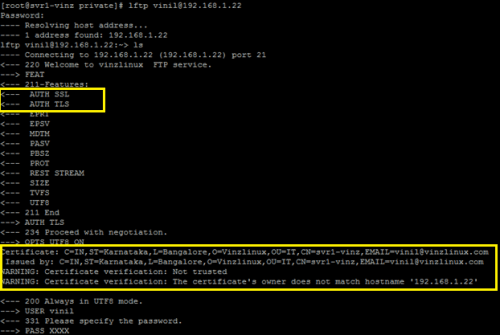
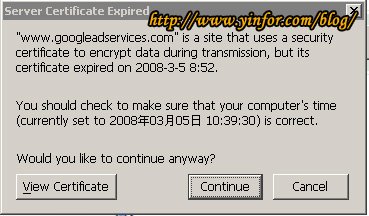
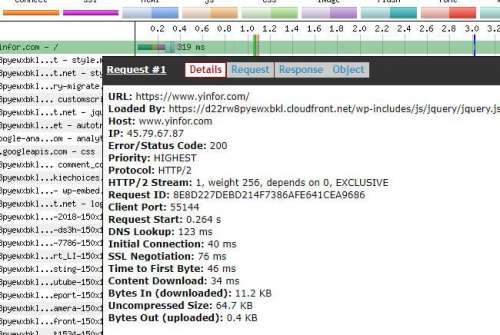
After installing the SSL certificate on the Nginx web server, you need to check if it is installed correctly. I installed the SSL certificate two months ago. The Sectigo ECC certificate. Now I change the certificate files. Previously, I put...