It is the first time, I received the abuse alert form Burst.net, the VPS service provider.
They said there is some malicious content on my VPS. Their backbone providers found it and reported to them and Burst ask me to respond in 24 hours.
I click the like they provided. It is a picture. It is just an image file with jpg extension. I can open it in the browser. But I want to do even more to investigate.
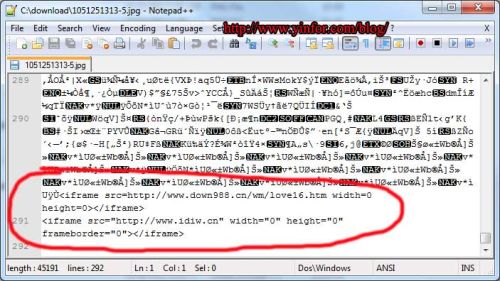
So I download it and use Notepad++, which is a free open source text editor software, to open it. At the end of the file, the harmful content is shown as below:
Now it is clean, one user of the website upload the picture file to website. He may not know it has problem. He may got it from the other site.
I open the jpg file with Photoshop, and save as another file. Then upload it to overwrite the old file on web server.
After that, I click rescan button on http://www.c-sirt.org site. Later the result is green. Incident is solved.
The second part of Burst.net email said I have to respond in 24 hours. So I reply the email to abuse@burst.net. Tell them what I did.
The url in the email is just one jpg file. I think maybe more than one has same issue. So I download all jpg files from the upimg folder, which stores all images files uploaded by site users.
Notepad++ has a function, call Find in files. Search “iframe” in all files under this folder including sub-folders.
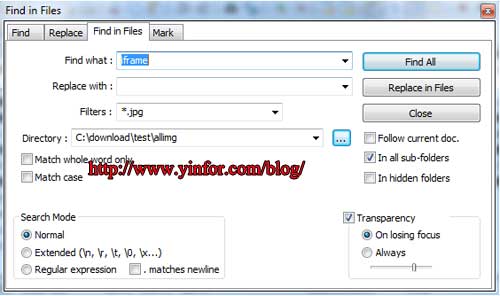
The result is that I found 4 more jpg files with same iframe code.
The solutions is download it, photoshop open it, save as it, upload and overwrite it. Done.