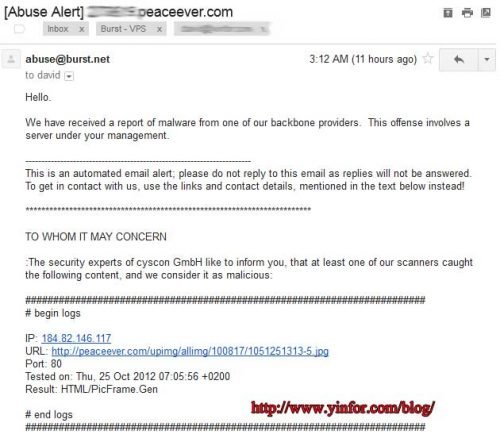
Report the bad IP address to the AbuseIPDB
I have a VPS on DigitalOcean. Web server is Nginx web server. I checked the web server log files, including an access log and error log. The error log always gives information about the strange activities from some IP address....