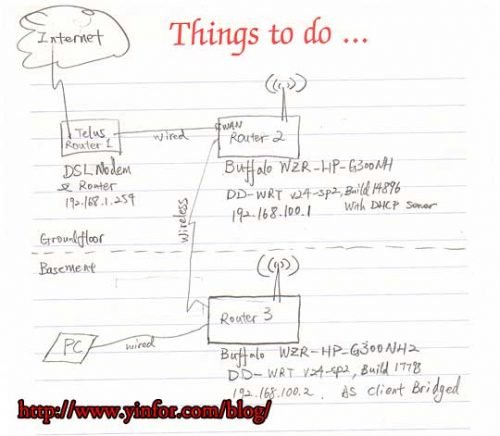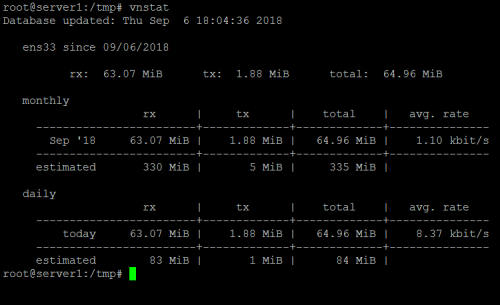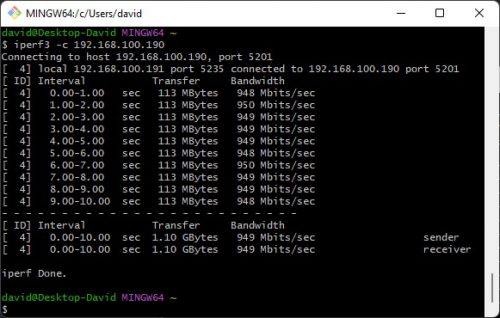
Realtek Driver is better than Microsoft Windows 11 driver
My PC has a network card or a Realtek 2.5GbE Network card. For a long time, I am using the network driver provided by Microsoft, which is from Windows 11. Recently, I think I can try the Realteck official driver,...