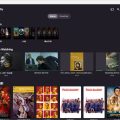
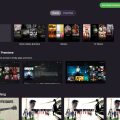
If you saw my previous post about my NAS which is powered by Ubuntu 22.04LTS, you should know that I have an Emby server running on the NAS system. It is time to upgrade it to the latest version, or v4.7.12.0.
Today, I sign in to the Emby server and look at the Dashboard. It said there is a new version available.
The latest version is at https://github.com/MediaBrowser/Emby.Releases/releases
For me, I download the deb amd64 edition installation package.
So, sign in the NAS in the terminal window through PUTTY.
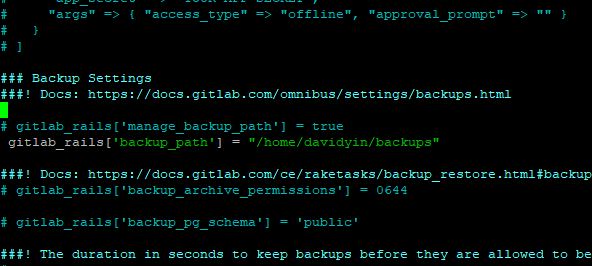
Run the following command to upgrade Emby.
cd ~ cd ~ wget https://github.com/MediaBrowser/Emby.Releases/releases/download/4.7.12.0/emby-server-deb_4.7.12.0_amd64.deb sudo systemctl stop emby-server sudo dpkg -i emby-server-deb_4.7.12.0_amd64.deb sudo systemctl start emby-server
Wait for the Emby server to load in a few minutes.
There is a piece of very bad news for Emby server Security advisory 2023-5-25. Someone’s Emby is hacked through an open public Internet connection.
Starting Mid-May 2023, a hacker managed to infiltrate user-hosted instances of Emby Server which were accessible via public internet and had an insecure configuration for administrative user accounts. Combined with the “Proxy Header Vulnerability”, which was recently fixed in the beta channel, this allowed an attacker to gain administrative access on such systems. Eventually, this allowed the attackers to install a custom plugin of their own, which establishes a backdoor in the running process of Emby Server.
After careful analysis and evaluation of possible strategies for mitigation, the Emby team was able to push out an update to Emby Server instances which is able to detect the plugin in question and prevents it from being loaded. Due to the severity and the nature of this situation and in an abundance of caution we are preventing affected servers to start up again after the detection, even with the plug-in being locked out, as all data and user accounts need to be considered as compromised. As the given situation requires direct action and assessment by the administrator, we determined that shutting down the server and preventing further startup up is the most suitable action as it disables the plug-in, possibly prevents the situation from getting worse and at the same time draws the attention of the administrator onto the subject.
Analysis of the plug-in has revealed that it is forwarding the login credentials including the password for every successful login to an external server under control of the hackers.
I am always suggesting that any services running inside of your house, or a homelab, should not allow access from the public Internet. If you really need to access the service from outside of your LAN, just open the port for this service and limit the IP which can access it. Of course, the username and password is a must.