It is Automatic Black-List with PAM module, which can help you to protect SSH server.
I have Centos 5.5 linux server on Butstnet.
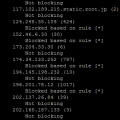
From log file, I saw a lot of fail login on my SSH server every day.
To save the resource and block them, I google and got the idea to install PAM-abl to stop them.
I just noted here for my experience.
1) install pam devel package
yum install pam-devel
2) Download PAM-abl v 0.4.1 from the sourceforge
wget http://sourceforge.net/projects/pam-abl/files/pam-abl/0.4.1/pam-abl-0.4.1.tar.bz2/download
3) Untar it
tar xjvf pam-abl-0.4.1.tar.bz2
4) Compile
cd pam-abl-0.4.1 ./configure make make check make install
5) Enable it
Make sure you have the following line in your /etc/ssh/sshd_config configuration file.
UsePAM
Next, add a line like the following in the file /etc/pam.d/sshd before the existing auth lines:
auth required /usr/local/lib/security/pam_abl.so config=/etc/security/pam_abl.conf
Edit /etc/security/pam_abl.conf file:
# Black-list any remote host with 10 consecutive authentication failures # in one hour, or 30 in one day. Keep them in the black-list for two days # and then purge them. host_db=/var/lib/abl/hosts.db host_purge=2d host_rule=*:10/1h,30/1d # Black-list any local user other than root for which there are 10 # consecutive authentication failures in one hour, or 30 in one day. # Keep them in the black-list for two days and then purge them. # Note that this means that non-root users may be subjected to denial of # service attacks caused by remote password guessing. user_db=/var/lib/abl/users.db user_purge=2d user_rule=!root:10/1h,30/1d
Then, make sure you have the folder /var/lib/abl/, otherwise the file hosts.db can not be created.
Partial content of this post is based on this link.