I have any VPS which is hosted on Burst.net.
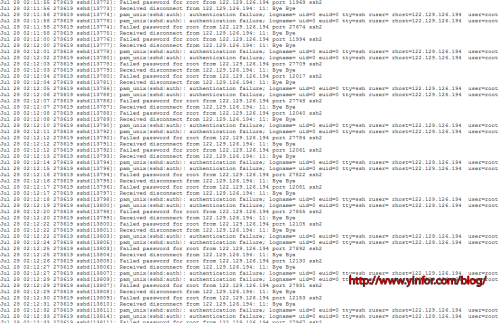
The openssh server running on it. When I checked the error log. I saw a lot of log in errors as below.
It is clear that the hacker want to connect this VPS through SSH as root. They tried different password, different port. All were blocked by PAM system.
To save the cost of these connection and PAM. I choose the way to block them per IP address.
It is TCP Wrappers,
I config it as below. Block all IPs to SSH, except my own IP address.
Allow access to sshd service only via /etc/hosts.allow:
sshd : 192.168.1.2
2
Deny everything via /etc/hosts.deny:
sshd : ALL
Then, after one day, I check the error log.
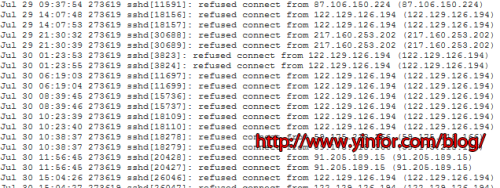
That is how to block SSH connection per IP address. Also one of the best practice to protect SSH service.